Which of the Following Are Real-life Examples of Cyber-attacks
Sony PlayStation Network DDOS Attack 4. In January 2022 Bleeping Computer described a sophisticated phishing attack designed to steal Office 365 credentials in which the attackers imitated the US Department of Labor DoL.

Hundreds Of Businesses From Sweden To U S Affected By Cyberattack The New York Times
Web-based delivery attacks are also called Man-in-the-Middle attacks.

. Persuasive email phishing attack imitates US Department of Labor. While there are many different ways that an attacker can infiltrate an IT system most cyber-attacks rely on pretty similar techniques. Here are some common cyber-attack examples.
Hacking a pacemaker to deliver an 830 volt shock enough to kill a would-be victim. These incidents also showcase how a single attack can harm a company. Curch of Scientology Attacked 7.
In 2012 researcher Barnarby Jack provided a real-life demonstration of what had been a theoretical risk for years. The attacker gained access to the employees email accounts resulting in the exposure of the personal details of over 100000 elderly patients. MafiaBoy DDoS Attack on Amazon eBay CNN 8.
Cyberattacks DDoS Threats to Air Transport Industry. Adobe announced in October 2013 the massive hacking of its IT infrastructure. Pharming involves phishing campaigns that involve redirecting users to fraudulent websites to submit sensitive information.
WannaCry Ransomware Attack 2. Below are a few examples of companies that have fallen victim and paid a high price for it. Below are some of the most common types of cyber-attacks.
The ranking is presented in increasing order of impact based on number of victims. Here is our Top 10 of the worlds largest cyberattacks 10. Ukraine was hit by a variety of cyberattacks in the run-up to Russias invasion of the country in February 2022 including massive distributed-denial-of-service DDoS data wiper and ransomware attacks.
There is strong evidence that the public transportation system needs dramatic investments in order to stay safe and sound from cyberattacks and the following three examples serve as real-life examples of what already exists and has occurred. MITM is one of the most common types of attacks that allow cybercriminals to intercept a network through a vulnerability. Bangladesh Bank Cyber Heist 3.
Voice calls voice messages. Lets first take a look at reasons why employees become inside attackers. Types of CyberAttacks Top 10 Largest Cyber Attacks in the World 10.
Example of Email Phishing The Daily Swig reported a phishing attack that occurred in December 2020 at US healthcare provider Elara Caring that came after an unauthorized computer intrusion targeting two employees. South Korea Credit Cards Data Compromise 9. PayPal is one of the most often impersonated brands.
HBGary breach hackers related to the Anonymous activist group used SQL Injection to take down the IT security companys website. Here are the five most common types of cyber-attacks. Ransomware attacks on Ukraine deemed a decoy for other cyber threats.
7-Eleven breach a team of attackers used SQL injection to penetrate corporate systems at several companies primarily the 7-Eleven retail chain stealing 130 million credit card numbers. They illustrate common motivations for attacks and sources of insider threats. In 2015 in Ukraine a variant of the BlackEnergy malware made the first known successful cyberattack on a power grid disabling 30 substations and leaving hundreds of.
15 Common Types of Cyber Attacks. Phishing Phishers send emails that appear to come from trusted sources with the goal of stealing personal information from unwitting users or influencing them to engage in a detrimental action like clicking on a link or sharing financial information. The attacker then secretly spies on every communication which is made between a server and a client user.
Vishing attacks involve voice as an attacker vector ie. 5 cases of insider attacks and their consequences. Smishing attacks utilise phishing user information via SMS or text messages as attack vectors.
Adobe was going through hell. Ashley Madison Data Breach 5. Having no cyber security plan for you or your business is like a bank with an open vault.
Weve selected five real-life cases of insider attacks. Knowing what kind of attack criminals can use. Malware is a type of application that can perform a variety of malicious tasks.
The scam is a noteworthy example of how convincing phishing attempts are becoming.

Ukraine Crisis Wiper Discovered In Latest Cyber Attacks Bbc News
What Is An Attack Surface And How To Protect It

Cool Powerful Cyber Security Resume To Get Hired Right Away Check More At Http Snefci Org Powerful Cyber Secu Security Resume Resume Examples Cyber Security

Cyber Security Infographic Template Cybersecurity Infographic Cyber Security Free Infographic Templates

8 Most Common Cybersecurity Threats Types Of Cyber Attacks Cybersecurity For Beginners Edureka Youtube

What Are The Most Common Types Of Cyber Attacks Infographic
Top 10 Most Common Types Of Cyber Attacks

Pin On Life At Peter Bowey Computer Solutions

How To Prevent Phishing Attacks On Your Company Real Life Examples And Tips Corporate Security Prevention Work Organization
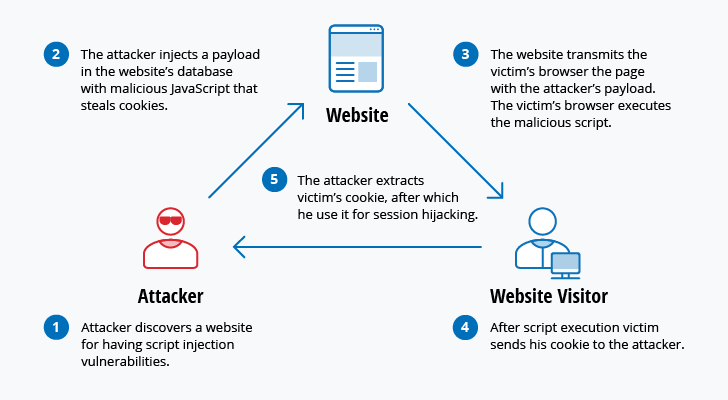
What Is Cyber Warfare Types Examples Mitigation Imperva

The Osi Model And Cyber Attack Examples Originally Published In Download Scientific Diagram

10 Biggest Cyber Attacks In History Clear Insurance

Cyber Incident Response Fast Attack Recovery Bit Sentinel
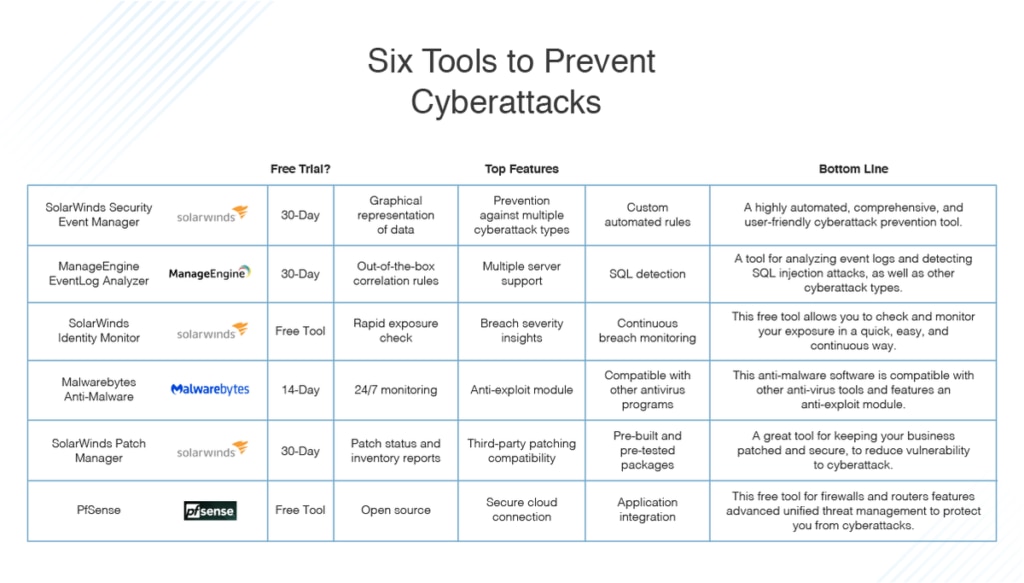
Top 6 Common Types Of Cyberattacks Dnsstuff

Top 20 Most Common Types Of Cyber Attacks Fortinet

Top 10 Cyber Threats World Is Facing In 2021 Cyber Threat Threat Cyber

Infographics Social Engineering Tactics To Protect Your Data And Privacy From Social Attacks Infograph Cyber Security Awareness Cyber Security Infographic


Comments
Post a Comment